You’d think by now we’d have it all figured out. But talk to anyone running point on vulnerability management, and you’ll hear the same story: backlogs that never shrink, findings that never make it to fix, scanners firing off alerts no one trusts. Somewhere along the way, visibility became the goal instead of resolution. And that’s precisely where attackers thrive.
Nearly a quarter of vulnerabilities are exploited before a patch even exists. That means attackers aren’t just relying on slow patch cycles—they’re getting ahead of them. They're not waiting for you to miss a fix; they’re counting on a system where response isn’t built in from the start.
This isn’t about buying another tool or building a better dashboard. It’s about building an accountable system from end to end, so that when something is found, it gets fixed.
What a Vulnerability Management Program Is
A real vulnerability management program isn’t a set of tools, but a system of execution. It governs how findings are disseminated across various environments and organizational boundaries and how risk is mitigated. That system has to function in places where things rarely stay still: ephemeral workloads, shifting repos, and cloud resources that exist for hours, not months. It needs to survive organizational changes, tool swaps, and the reality that no two teams work the same way.
And that’s why most programs don’t work. They aren’t programs but a series of disconnected steps with no feedback loop. Scanners flag issues, tickets get filed, and weeks later, no one can tell whether the fix was deployed, whether the asset still exists, or who was responsible for the care.
A working program doesn’t just identify risk but closes it. That means resolving ownership automatically. Normalizing signals across tool outputs and prioritizing based on exposure and impact, rather than severity labels, and tracking the fix all the way through. It’s not about having the best scanner. It’s about making the system accountable for outcomes.
Visualizing the shift from fragmented tools to unified, closed-loop vulnerability management that ensures ownership, accountability, and risk resolution.
Building a Functional Vulnerability Management Program With 7 Essential Components
So, what does a functional vulnerability management program look like in practice? Not as a theory, but as a system that consistently closes risk. It’s not built through policy or good intentions, but through seven core components, each addressing a specific operational failure that most teams encounter. If even one is missing, the whole system breaks. Let’s unpack them.
1. Live Asset Inventory With Ownership Mapping
Every remediation workflow begins with one fundamental question: What is this, and who is responsible for it? If you can’t answer that in real time, every downstream action, triage, prioritization, and assignment will grind to a halt.
Most teams still rely on spreadsheets, outdated CMDBs, or informal knowledge bases to map assets to owners. But modern infrastructure doesn’t work that way. Services deploy across cloud regions, containers live for minutes, and the same app might run under five different names depending on who last touched it. Static inventory guarantees blind spots.
DevOcean was built with this reality in mind. It continuously pulls data from your existing systems and resolves every finding to a live, queryable graph of services and owners, with no manual mapping or guesswork. If a scanner flags an issue in a transient container tied to a shared VPC in a development account, the system still knows where it came from and who is responsible. Because if you have to ask around to figure out who owns a vulnerability, you’re already too late.
2. Unified Ingestion and Normalization of Findings
A functioning vulnerability management program isn’t built on top of a single scanner. It has to work across dozens. For example, SAST for code, DAST for services, CSPMs for cloud, container tools for infrastructure, and IaC scanners for configuration drift. Every layer adds more findings, and none of them agree. Without normalization, you don’t have a program, and you have overlapping reports and an impossible queue. That’s precisely what unified vulnerability management is designed to solve by bringing structure to scattered, multi-source findings.
It is where most programs stall. Findings arrive fragmented, duplicated, and inconsistent. One tool flags a library, another flags the image that includes it, and a third flags the container running that image. Without correlation, they are treated as three separate issues. Without deduplication, they appear on three dashboards. And without asset mapping, none of them are assigned to the right team.
3. Context-Aware Prioritization
Severity alone is a terrible way to prioritize. Most scanners will mark anything that matches a CVE with a high CVSS score as “critical,” and regardless of whether it’s exploitable, reachable, or even deployed in prod. The result: bloated backlogs full of noise, and teams wasting hours triaging issues that pose zero real-world risk.
A functional vulnerability management program doesn’t just queue up findings. It ranks them using context. Is the vulnerable asset exposed to the internet? Is it running in production? Does it have a known exploit in the wild? In certain industries like fintech, web application firewalls often serve as a first layer of defense when internet exposure is unavoidable. Without these signals and EPSS, reachability, and asset criticality, you’re not prioritizing but probably sorting alphabetically.
It is where most programs collapse into busywork. Hundreds of “critical” tickets with no meaningful risk, and truly urgent issues buried under the weight of false positives.
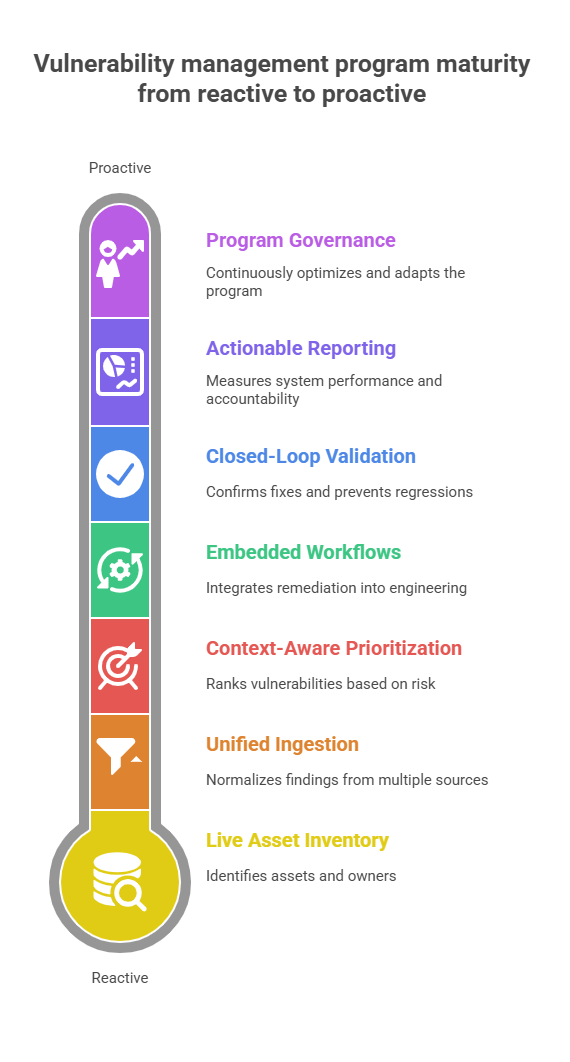
Seven key components that elevate vulnerability management from reactive scanning to a mature, proactive, and outcome-driven security program.
4. Embedded Remediation Workflows
No vulnerability gets fixed in a security dashboard. If your remediation process depends on engineers logging into a separate portal, parsing raw scanner output, and stitching together missing context, the fix won’t happen. That’s why teams are increasingly exploring AI test automation to accelerate both validation and handoff at scale. Or it’ll take weeks longer than it should.
A robust vulnerability management program integrates issues directly into engineering workflows and includes all necessary components to take action. Not just the CVE or severity, but the entire context, including the affected service, environment, exposure details, ownership, and guidance on how to resolve it.
That handoff can’t be manual and has to be systemic. That’s what a unified vulnerability remediation management platform enables: clean, enriched findings pushed into the right backlog, assigned to the right team, linked to the exemplary service and repo. So devs don’t need to go digging. They just get to work.
5. Closed-Loop Fix Validation
In most organizations, a vulnerability is considered “fixed” the moment a ticket gets closed. But in a real vulnerability management program, that’s just the midpoint.
Fix validation isn’t about tracking tickets, it’s about confirming outcomes. But vulnerability remediation often breaks here, especially when validation steps aren’t automated or consistently enforced
It is where many programs fail silently. Teams push commits that never make it to prod. Containers get rebuilt with old base images. Infrastructure changes get rolled back without notice. The finding disappears from the queue, but the exposure remains in place. And no one knows until it resurfaces in an incident and or an audit.
6. Actionable Reporting and Metrics
Most teams can tell you how many vulnerabilities they scanned last month. But without adhering to vulnerability management best practices, there’s often no visibility into how many were fixed or how long it took.
A functioning vulnerability management program doesn’t just generate reports. It measures how well the system is working. That means tracking time to remediate from detection to verified fix. It means showing what percentage of findings were assigned to an owner. It means exposing SLA adherence per team, per service, per environment, and so you can see where accountability stalls. These are operational metrics.
A unified vulnerability remediation management platform makes this visibility native. Because the data isn’t buried in disconnected tools and it’s stitched together from detection through closure, with ownership and timestamps intact.
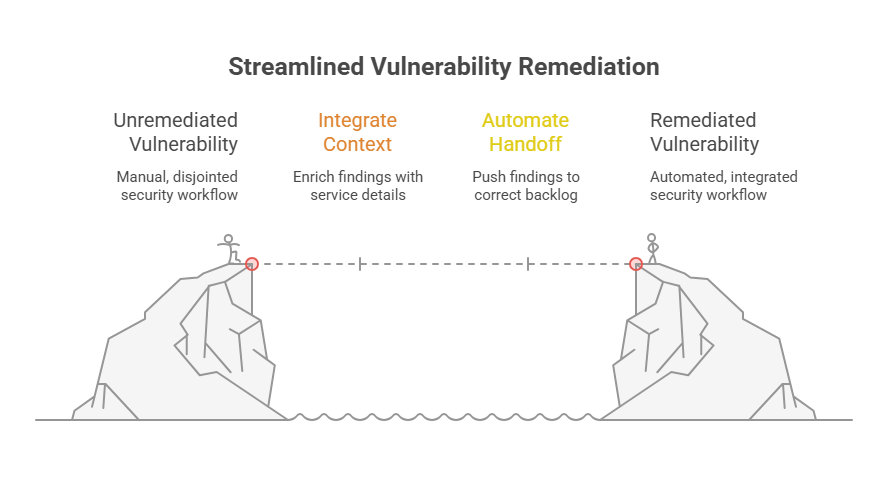
A side-by-side comparison of manual vs. automated vulnerability remediation workflows, highlighting the need for streamlined, contextual, and scalable security fixes.
7. Program Governance and Continuous Optimization
Even the best-designed vulnerability management program will fail if it’s treated as a static system. The environment changes. Team structures evolve, tools get replaced, and without deliberate governance, the entire program drifts. No one notices until the gaps show up in an audit or a breach report.
Strong programs adapt, and that doesn’t mean adding bureaucracy, but more building regular retrospectives across security and engineering, and reviewing remediation metrics to identify systemic slowdowns. Additionally, it involves tuning SLAs when service criticality shifts and revisiting prioritization policies when exploitability models change. And doing all of it with cross-functional input, not in a silo. That alignment is especially important as regulations increasingly shape expectations for AI risk management across security and compliance teams.
A unified vulnerability remediation management platform provides data with traceability to support this. It displays trends, SLA heatmaps, and backlog breakdowns by service, making it all visible and accessible. Because a program that can’t inspect itself can’t improve, and one that doesn’t improve won’t last.
The System Will Fail Unless It’s Built to Carry the Weight
Vulnerability management doesn’t break at the edges. It breaks at the handoffs and between scanners and services, between teams and tickets, between intent and execution. And most programs are made of fragile handoffs.
What you’re left with is a system that looks functional from a distance: scans run, issues get filed, and dashboards show progress. But underneath, ownership is missing. Priorities are wrong. Nothing loops back. And eventually, the work stops being real.
A vulnerability management program only works when every piece supports the next. That doesn’t happen by duct-taping tools together. It happens when the system itself and what connects ingestion to closure are designed to hold the operational weight. That’s the difference a unified vulnerability remediation management platform makes. DevOcean isn’t here to replace your stack. It’s here to give it structure.
If your program isn’t working, it’s not because people aren’t trying. It’s because the system can’t carry the load. DevOcean changes that.
The true cost of poor security remediation.
Goes beyond wasted resources, overspent budgets, and missed SLAs.
Stay ahead of breaches - get started with DevOcean.
.png)


%20Breach.png)
.png)
