Most teams don’t struggle with detection — they struggle with what comes after. Scanner alerts keep piling up, and triage becomes a bottleneck. Ownership gets murky, priorities blur, and tickets quietly age in the backlog while everyone assumes someone else will handle them.
According to IBM, attackers exploited vulnerabilities in over one-quarter of the incidents they responded to, with slow patch cycles and outdated systems being major contributors.
Vulnerability management as a service helps teams cut noise, focus on real risk, and prove fixes work. This guide shows you exactly what proper vulnerability management as a service looks like, how to recognize it, and how to choose a provider who delivers on that promise.
What Is Vulnerability Management as a Service (VMaaS)?
Vulnerability Management as a Service (VMaaS) is an operational layer that takes the flood of findings you generate and drives them to closure. It aligns closely with how vulnerability management as a service is delivered across the industry, emphasizing outcomes over alerts. Instead of selling you more alerts, VMaaS focuses on outcomes: fewer repeated vulnerabilities, faster remediation cycles, and a clear record of what was fixed and validated.
In practice, that means the whole lifecycle is covered. Findings are ingested from scanners and asset managers, triaged for relevance, prioritized by real risk, and then assigned to the right owners. VMaaS integrates directly with developer workflows, so tickets land in the right backlog with the right context. When fixes ship, the service validates remediation and closes the loop. What used to be a manual chase involving emailing teams, juggling spreadsheets, and chasing SLAs becomes a structured, measurable process.
For security operations, this shift matters. It moves you from tools to service, and from service to business outcomes. Engineers spend less time arguing about ownership, AppSec teams stop drowning in false positives, and leaders can confidently report progress.
VMaaS Focus and Impact
What to Look for in a Vulnerability Management as a Service Provider
Choosing a vulnerability management as a service provider isn’t about who has the most features. Features look good in demos, but what really matters is whether the provider can take the noise from your scanners and translate it into fixes that stick. A solid foundation begins with the essential components of a vulnerability management program, which shape how well a provider can turn detection into durable remediation.
You should ask the question: Does the service collapse under complexity, or does it give you a repeatable path from detection to resolution?
Here are six traits you should consider when evaluating Vulnerability Management as a Service.
1. Ingestion That Cleans Up the Noise
Most security teams already know the pain of duplicate findings. One scanner says “critical,” another calls it “high,” you’re left reconciling differences instead of driving remediation. A strong provider ingests results from every scanner and asset source you have, then normalizes and deduplicates them. That means one clean list to work from, not endless debates about which tool is right. Without this, your backlog will always grow faster than you can close.

Refining Vulnerability Management
2. Prioritization That Reflects Real Risk
Severity scores are blunt instruments. If everything looks “critical,” nothing truly is. A capable vulnerability management as a service provider will enrich findings with context: exploitability in the wild, exposure in your environment, and the value of the affected asset. It is how you separate the vulnerability in a sandbox test box from the one in production customer data paths.
Strong prioritization turns a mountain of tickets into a shortlist that makes sense to security and engineering. This risk-based approach is increasingly paired with offensive cybersecurity, where simulated attacks test whether the right vulnerabilities are being surfaced and addressed.
3. Automatic Ownership Assignment
This is where most backlogs stall. Findings pile up because no one knows who should fix them. A good provider automates ownership assignment, mapping each issue to a service owner, repo maintainer, or platform team.
The accountability extends beyond people; managing non-human identities like service accounts and machine credentials is equally critical to preventing unresolved risks from growing silently. Done right, the vulnerability doesn’t just land in a queue; it lands in the correct queue, with the proper context, so it doesn’t age into risk. This reduces the “lost in translation” lag between security teams and developers and ensures accountability.
4. Integration Into Developer Workflows
Developers don’t need another dashboard. They already live in Jira, GitHub, GitLab, or Azure DevOps. An effective provider will integrate directly into those systems, pushing vulnerabilities into tickets that carry business and security contexts. That integration turns a security issue into another piece of engineering work, planned, prioritized, and tracked like everything else. Without this, security stays a parallel process that developers are more likely to ignore.
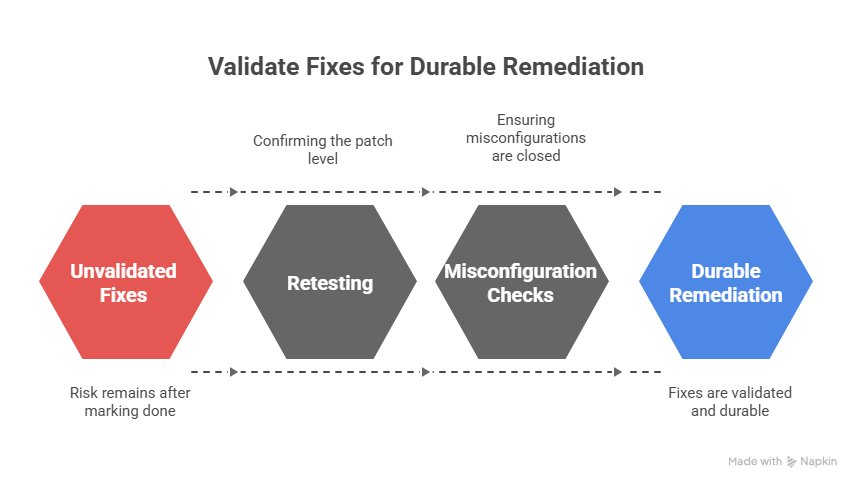
Validate Fixes for Durable Remediation
5. Validation That Fixes Hold
Marking a ticket “done” doesn’t mean the risk is gone. A strong vulnerability management as a service provider validates the fix by retesting, confirming the patch level, or checking that misconfigurations are closed. This is where audit and compliance value come in.
If fixes aren’t validated, the same issue can creep back into the next release cycle, erasing progress and frustrating both security and engineering teams. Validation makes remediation durable, not temporary.
6. Reporting That Proves Progress
Executives and boards don’t care about the raw number of alerts ingested; they care about whether the backlog is shrinking, whether the mean time to remediate is improving, and whether repeat issues are going down. These are the exact visibility needs that shape broader security areas like insider threat detection, where progress is measured less in alerts and more in meaningful risk reduction.
The right provider offers outcome-based reporting, not vanity metrics. It allows security leaders to show progress in terms that matter to the business: resilience, accountability, and reduced exposure.
When Does Vulnerability Management as a Service Make Sense?
There are clear signs you’ve outgrown scanners and manual workflows. If these sound familiar, it’s time to think about a platform-level solution:
- Your backlog never shrinks. Every scan adds hundreds of new findings, but ownership is unclear, and old tickets linger for months.
- You’re chasing teams instead of managing risk. Security spends more time emailing developers and updating spreadsheets than driving fixes.
- Prioritization feels like guesswork. With everything labeled “critical,” it’s hard to know which vulnerabilities matter most to the business.
- Fixes don’t stick. You close tickets, but the same issues reappear in the next audit or release cycle.
- Executives ask for metrics you can’t provide. You can show scan counts, but not time-to-remediate, closure rates, or reductions in repeat issues.
These are daily operational drags that slow down engineering and security. Vulnerability management as a service makes sense once the pain of juggling tools, ownership gaps, and endless backlog outweighs the cost of a managed workflow. At the same time, organizations are increasingly broadening their lens to exposure management, which helps contextualize vulnerabilities into the broader attack surface. At that point, the investment pays off in clarity, accountability, and the ability to show real progress.
7 Questions to Ask Before You Choose a Vulnerability Management as a Service Platform
The proper vulnerability management as a service provider should make remediation easier, not harder. When you evaluate platforms, these questions will separate the real solutions from the marketing fluff:
- How do you assign ownership for each finding? Clear, automated assignment prevents vulnerabilities from getting stuck in limbo. The best providers map directly to service owners or teams.
- Can you ingest and normalize findings across scanners and assets? Without this, you’ll be stuck reconciling conflicting alerts. Normalization ensures one clean, trusted list.
- Do you group or deduplicate findings by root cause? Grouping avoids fixing the same issue five different ways and helps reduce backlog noise.
- Can I track remediation through to validation or closure? Closing a ticket isn’t enough; you need proof that the fix worked.
- How do you prioritize findings by risk, not just severity? Look for context-based ranking that reflects exploitability and business impact.
- Can we integrate into our existing ticketing and dev tools? If developers need new workflows, adoption will stall. Integration into Jira, GitHub, or GitLab is essential.
- What metrics can I report to leadership that show real progress? Ask for outcome metrics like mean time to remediate and repeat issue rates, not vanity counts of alerts ingested.
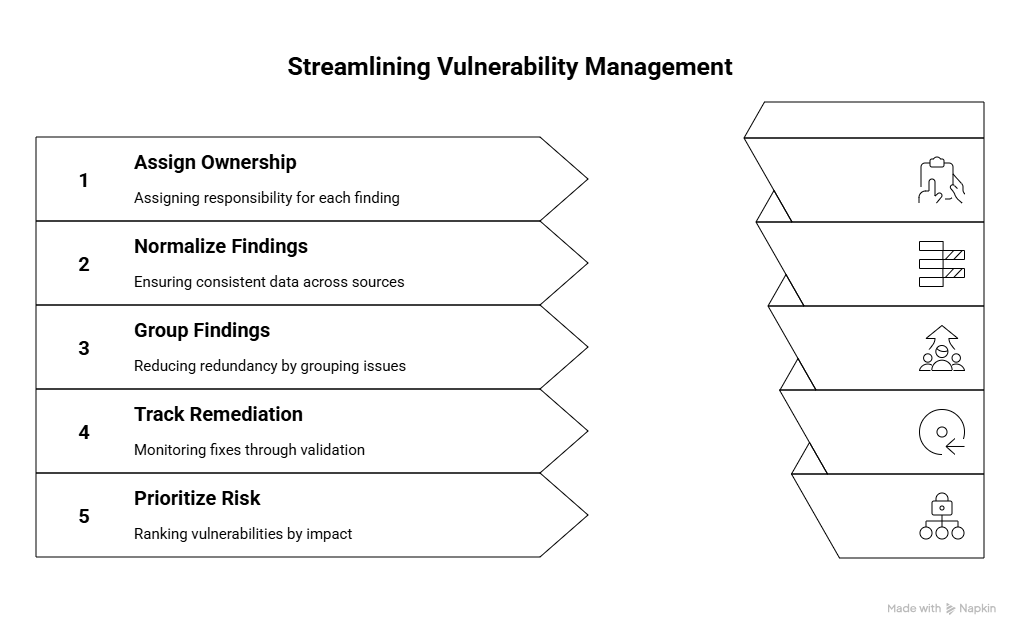
Streamlining Vulnerability Management
How DevOcean Delivers Modern Vulnerability Management as a Service
DevOcean is built around a simple promise: take the chaos of vulnerability detection and turn it into predictable, managed remediation. The platform takes the findings you already have and drives them through the entire lifecycle, from ingestion to validation, without forcing teams to change how they work.
Findings from scanners and asset managers flow into DevOcean, where they’re normalized, deduplicated, and prioritized based on real business risk. Ownership is assigned automatically, so issues land with the right team the first time. For developers, vulnerabilities appear as actionable tickets inside Jira, GitHub, or GitLab, not as disconnected spreadsheets or emails. For security teams, it means no more chasing down who’s responsible.
Every fix is tracked through to validation, closing the loop and reducing the chance of repeat findings. Progress is measurable in terms that leaders care about: time to remediate, backlog reduction, and fewer recurring issues. The result is a security program that spends less time fighting noise and more time building resilience. DevOcean delivers vulnerability management as a service in the way modern engineering teams need it, focused on outcomes, embedded in workflows, and built for continuous improvement.
Turn Vulnerabilities Into Wins
Vulnerability management as a service is about turning detection into resolution. The difference is measurable through fewer repeats, faster fixes, and accountability you can prove.
The next step is putting that clarity into practice. DevOcean is built for embedding ownership, prioritization, and validation directly into your teams' workflows. Aligning remediation with existing tools and processes, it removes friction while strengthening outcomes. The result is a culture shift where resolution becomes routine, not an exception. Ready to see it in action? Book a walkthrough with DevOcean and discover how quickly your vulnerability management program can turn from reactive into a driver of resilience.
The true cost of poor security remediation.
Goes beyond wasted resources, overspent budgets, and missed SLAs.
Stay ahead of breaches - get started with DevOcean.
.png)

.png)
%20Breach.png)

