The promise of cybersecurity platforms is clear: visibility, control, and confidence. However, for many teams, the daily reality is more complex. They’re flooded with alerts, buried in tool sprawl, and stuck managing risk with spreadsheets and hope. It isn’t a failure of effort; it’s a sign that the current model isn’t working. And in today’s environment, that disconnect carries real consequences.
Only 3% of organizations globally qualify as “Mature” in their cybersecurity readiness. Even more revealing is that 73% expect a significant cyber incident within the next two years, but 80% still express confidence in their ability to withstand it. The gap between belief and preparedness is not just wide, it’s hazardous.
If cybersecurity is going to keep up with the scale and speed of today’s threats, it needs to be operationalized from the inside out. That starts with rethinking how security work gets done.
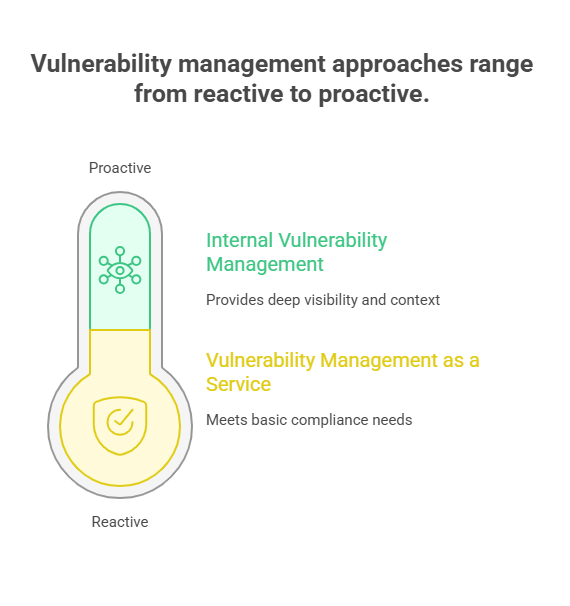
Compare VMaaS vs. internal vulnerability management: move from reactive compliance to proactive security with deep context and continuous visibility.
What Is Vulnerability Management as a Service?
Vulnerability Management as a Service is the outsourced delivery of scanning, assessment, and reporting functions that identify security weaknesses across your systems.
On paper, it promises relief:
- External experts handle scheduled assessments,
- run network and application scans,
- generate tickets, and,
- deliver reports with recommended remediations.
Most providers operate on a schedule of monthly or quarterly scans, templated findings, and periodic consulting calls to review results. For overburdened security teams, it offered a stopgap. Hiring was difficult, compliance demands were rising, and something had to be in place.
That context explains the popularity. Many teams adopted Vulnerability Management as a Service, not because it was excellent, but because the alternative was doing nothing, especially when trying to meet growing regulatory requirements such as ISO 42001 compliance. Teams used it to signal to regulators and executives that they had security under control.
Over time, however, the limitations have become increasingly difficult to ignore. The fixed cadence leaves zero-day risks and newly exposed assets unscanned for weeks. The findings are often shallow, with minimal context for triage or technical nuance. Ticket handoffs can flood engineering queues with low-value tasks that feel disconnected from real risk. Worse, an external vendor owns the entire process, leaving minimal visibility into what has changed or improved.
What You’re Getting with Vulnerability Management as a Service
You get the monthly PDF. Maybe a login to a dashboard, if the provider offers one. However, it is usually static, with no real-time data and no way to drill into what has changed since last week. The report lists what was scanned and found, but overlooks what matters and what has already been resolved.
Then come the tickets. Hundreds of them, often dumped into Jira with the same priority tag. The system lacks contextual triage, awareness of your environment, and insight into which teams can respond.
There is also the question no one likes to answer: who owns what? The system adds findings to your backlog, but leaves ownership within your organization unclear. Security passes it to engineering. Engineering says they need more detail. Infrastructure claims no one consulted them, and you’re left caught in the middle.
These services rarely integrate cleanly with how your teams work. You cannot filter by team, by business unit, or by application owner. You cannot slice findings by historical trends or connect them to open incidents. Customization is limited, and changes are slow to implement.
Vulnerability Management as a Service may promise control, but rarely delivers the depth needed to drive real impact.
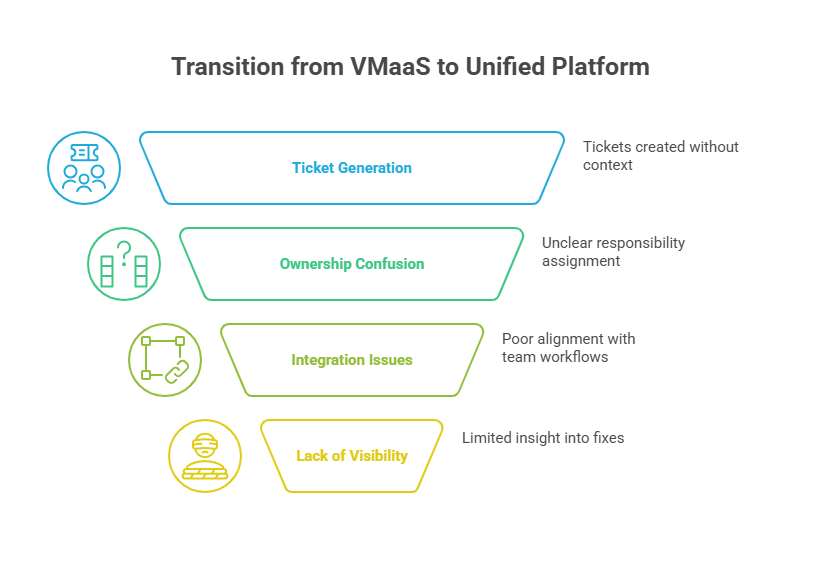
VMaaS pain points visualized: lack of ownership, ticket overload, poor integration, and limited visibility slow real risk reduction.
What You’re Still on the Hook For when it comes to Vulnerability Management as a Service
Buyers often assume Vulnerability Management as a Service will take care of the complex parts. But the moment the report lands, the real work begins, and it's still yours.
Can your provider tell you who owns this container in the staging environment? Can they see whether the asset is ephemeral, paused, or even still in use? Most cannot. Most traditional scanners identify assets by IP or hostname, not by service ownership, app logic, or deployment state, unless manually integrated with cloud metadata.
Can they verify that a fix has been shipped to production? Can they confirm it stayed fixed after the next deployment? That level of visibility resides within your CI/CD pipelines and infrastructure graph, not on the external scanning platform. These are critical gaps when dealing with real-world zero-day scenarios like CVE-2024-44308, where remediation windows are narrow and the stakes are high.
What about routing? If a vulnerability affects a shared service owned by the Platform, but the app team receives the alert, does anyone know who should take action? Can you trust that the right person even saw the ticket? Assigning ownership and ensuring accountability remain internal responsibilities, and most VMaaS providers lack native awareness of your org structure, unless you manually configure it, often at additional cost or complexity.
And then there’s the question leadership will ask: what changed? Are we getting better? Are we closing the risk? You will not get those answers from a flat list of findings. You need context, trends, validation, and alignment with what the business values.
Vulnerability Management as a Service can help identify and surface problems. However, it cannot dictate to your organization what to do, who should do it, or whether anything was effective, a limitation that underscores the rising focus on security remediation as a strategic priority going into 2025.
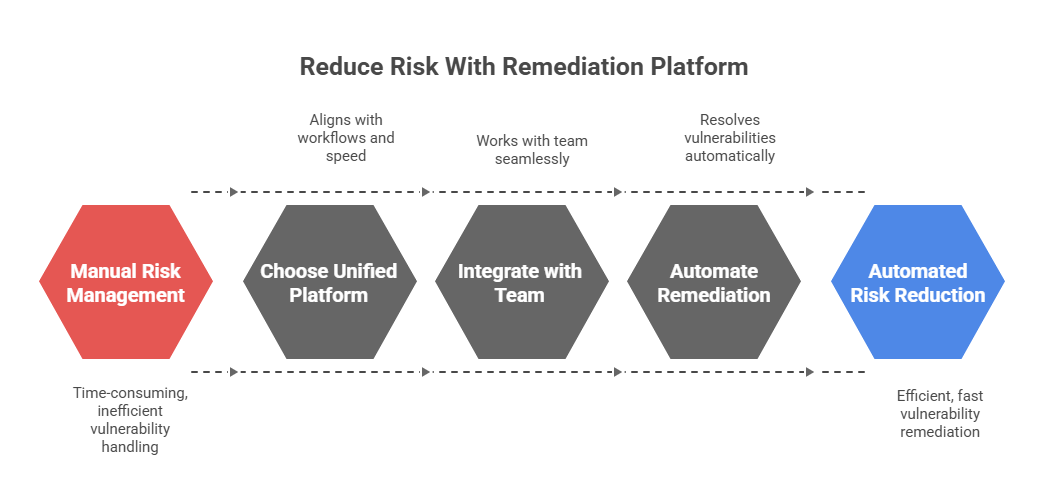
Upgrade from manual vulnerability handling to automated, team-aligned remediation with a unified platform built for speed, clarity, and security at scale.
The Alternative: Self-Service, Systemic, and Built for Resolution
You shouldn’t outsource vulnerability management. Instead, you should operationalize it. That means replacing the reactive, vendor-driven model with an internal system that runs continuously, adapts to your environment, and supports real resolution, not just detection.
Instead of juggling PDFs, ticket queues, and consultant calls, you start with a unified platform. It ingests vulnerabilities in real time and automatically enriches them with asset metadata, ownership signals, deployment state, and exploit intelligence. You see not just what’s broken, but where it lives, who owns it, and how urgent it is, making the case for a unified approach to vulnerability management that brings clarity to complexity.
The system resolves ownership automatically. Engineering tickets are created with clear context, linked back to the original finding, and routed to the right team. Fix validation happens downstream, across CI/CD and production. And every action, triage, suppression, and resolution is tracked. This alignment supports the broader shift toward embedding secure coding practices earlier in the development lifecycle, reducing the risk before it ever hits production.
Leadership gets outcome-driven reports tracking fix speed, team blockers, improvement trends, and risk reduction over time. The organization moves from “we scanned it” to “we fixed it and verified it.”
It is what most teams have been trying to cobble together: custom scripts, spreadsheets, tags, dashboards, and handoffs. But it doesn’t have to be duct tape. You can have a system that sees your environment the way you do and helps you act on it.
Why DevOcean Isn’t Vulnerability Management as a Service and Why That Matters
DevOcean is not a Vulnerability Management as a Service solution. It’s not a vendor you email, a queue you wait in, or a scheduled scan you hope captures the right thing. DevOcean is a unified vulnerability remediation management platform built to integrate into your environment.
How does it work? DevOcean takes the raw output of scanners and threat intelligence feeds, and turns those findings into structured, contextualized actions. Instead of handing you a generic ticket, it automatically routes the issue to the right person, along with metadata, ownership, asset state, and recommended next steps.
The result is a system that is faster, more transparent, and significantly easier to scale. You do not need to wait for the following consulting call to make changes. You don't need to dig through spreadsheets to see what was fixed. You get clarity, continuity, and confidence because DevOcean is designed for teams who are already in motion..
Rethink What You’re Paying For When It Comes to Vulnerability Management as a Service
Take a step back. What are you buying? Are you paying for outcomes or activity that appears to be progress?
Most Vulnerability Management as a Service providers document risk. They deliver findings, format tickets, and run scans. But documenting risk is not the same as reducing it. If your team still has to assign owners, chase down fixes, validate remediations, and explain progress to leadership, then what did the service solve?
If you are managing risk manually after paying for a solution, it was not a solution. It was a report generator with a support contract in place.
This is the moment to ask whether a service is the right model at all. What you need is not another vendor on a quarterly cadence. You may need a system. And that starts with choosing the right unified vulnerability remediation platform that aligns with your workflows, speed, and internal ownership models. One that works with your team, not around it. One that moves at the pace of engineering. One that resolves and does not detect the default.
Time to Trade the Report for Real Control
If you’ve felt the frustration of the endless findings, the unclear ownership, the slow handoffs, you are not alone. We have been in those rooms too, watching service-based models fall short while risk continues to pile up.
The problem is not that your team is underperforming. The problem is that the service model was never built for modern engineering environments. It produces tickets, not outcomes. It adds overhead, not clarity. And it forces you to manage risk manually, even after you’ve paid for help.
DevOcean was built to change that. It provides security and engineering teams with a shared context, automated ownership, real-time validation, and a clear view of what’s being fixed. No waiting, no guessing, no spreadsheets.
You do not need to outsource control to make progress. You need a system designed for the work you are already doing. DevOcean delivers that system. Start replacing the noise with progress. Try DevOcean for free.
The true cost of poor security remediation.
Goes beyond wasted resources, overspent budgets, and missed SLAs.
Stay ahead of breaches - get started with DevOcean.
.png)


%20Breach.png)
.png)
